 Keep Your Data Safe at an Airport – Avoid Juice Jacking!
Keep Your Data Safe at an Airport – Avoid Juice Jacking!
If you’re not careful about how you connect to Wi-Fi when you travel, you could be exposing your personal information to hackers. In fact, when you connect to free Wi-Fi at an airport, there are hackers trolling these connections and sometimes impersonating the networks. They want to get access to your credit card numbers, bank accounts, and other sensitive information.
How do they do it? They create fake networks that are named very similarly to the official airport networks. If you connect to one of these networks, they can spy on everything you do on your device. Whether it be a cell phone, tablet, or laptop, hackers can get into it.
In fact, anytime you connect to a certified airport network with no password, all of your data is sent to that network. Basically, anyone who wants to listen in can transmit data from your computer or phone across that network.

Avoid Juice Jacking!
Juice Jacking is when you use a public charging station to charge your phone, and a bad actor (hacker) uses it to steal data or load malware on your phone or device. Essentially, it’s a cyberattack.
Avoid plugging into random USBs and bring your own plug gear for outlets.
 If you need to get on the internet at an airport, be proactive and use these suggested tips to keep your data safe and still enjoy your trip:
If you need to get on the internet at an airport, be proactive and use these suggested tips to keep your data safe and still enjoy your trip:
- Forgo the airport network entirely. Use your cell phone’s hotspot feature.
- Use a Virtual Private Network (VPN). They slow down data speed, but make public Wi-Fi safer by ensuring that everything you do can’t be seen or modified by hackers.
- Enable multi-factor authentication
- Log out of apps when you are done using them. It’s harder for bad guys to get in if you are logged out.
Before you travel
- Backup your data in the cloud or on a portable hard drive.
- Use unique passwords. Include symbols and numbers.
Finally, make sure no one is “shoulder-surfing” (sitting behind you looking over your shoulder) your device content. Try using a security screen or lower the brightness to minimize visualization.
 Today, we honor the heroes who gave everything for our country. Their sacrifice is the foundation of the freedoms we protect every day.
Today, we honor the heroes who gave everything for our country. Their sacrifice is the foundation of the freedoms we protect every day.
 Today, on Peace Officers Memorial Day, we pause to honor the law enforcement officers who have made the ultimate sacrifice in the line of duty.
Today, on Peace Officers Memorial Day, we pause to honor the law enforcement officers who have made the ultimate sacrifice in the line of duty. Keep Your Data Safe at an Airport – Avoid Juice Jacking!
Keep Your Data Safe at an Airport – Avoid Juice Jacking!
 If you need to get on the internet at an airport, be proactive and use these suggested tips to keep your data safe and still enjoy your trip:
If you need to get on the internet at an airport, be proactive and use these suggested tips to keep your data safe and still enjoy your trip: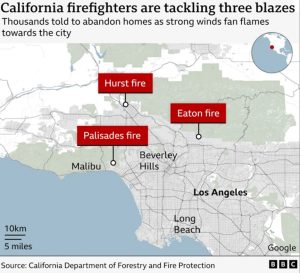
 The recent wildfires in Southern California have been devastating, with many people losing their homes and others facing significant disruptions to their lives.
The recent wildfires in Southern California have been devastating, with many people losing their homes and others facing significant disruptions to their lives. As we look back on this year, we’re reminded of how grateful we are to our law enforcement community and their families. Thank you for your support and for continuously inspiring us to do better.
As we look back on this year, we’re reminded of how grateful we are to our law enforcement community and their families. Thank you for your support and for continuously inspiring us to do better.  QR codes are everywhere! Signs, menus, and yes, parking. But, think twice before scanning one. There have been numerous reports about a scam involving fraudulent QR Codes in parking lots.
QR codes are everywhere! Signs, menus, and yes, parking. But, think twice before scanning one. There have been numerous reports about a scam involving fraudulent QR Codes in parking lots. Let’s be real. Scammers don’t seem to be slowing down any time soon. They will always be out there lurking for the next victim. And unfortunately, travelers are frequently targeted by scammers – particularly hackers. Your personal data is much more valuable than your personal items. But, with these simple steps, you can make it much harder for thieves to steal your information.
Let’s be real. Scammers don’t seem to be slowing down any time soon. They will always be out there lurking for the next victim. And unfortunately, travelers are frequently targeted by scammers – particularly hackers. Your personal data is much more valuable than your personal items. But, with these simple steps, you can make it much harder for thieves to steal your information. Let’s start with the basics. Gift cards are for gifts – not for payments. We buy gift cards to give to someone as a present. A birthday, a graduation, an anniversary, a holiday, a promotion, or other gift giving reasons. Never ever, under any circumstances, buy a gift card and then read the numbers to someone you don’t know over the phone. That has scam written all over it.
Let’s start with the basics. Gift cards are for gifts – not for payments. We buy gift cards to give to someone as a present. A birthday, a graduation, an anniversary, a holiday, a promotion, or other gift giving reasons. Never ever, under any circumstances, buy a gift card and then read the numbers to someone you don’t know over the phone. That has scam written all over it. Merry Christmas and Happy New Year from Privacy for Cops! We are grateful for the work we get to do every day in helping to protect law enforcement officers, publicly appointed officials, and their families, from the exposure of their personal information online.
Merry Christmas and Happy New Year from Privacy for Cops! We are grateful for the work we get to do every day in helping to protect law enforcement officers, publicly appointed officials, and their families, from the exposure of their personal information online. With respect, honor, and gratitude ~ Thank you to all those who served our beautiful country.
With respect, honor, and gratitude ~ Thank you to all those who served our beautiful country.